Going Digital: Digitally Signing Personally Identifiable Information (PII) Data and Consent
Digital Signatures
Activity Factory supports 2 types of digital signing.
- Document Cryptographic Hash
- Digital Signatures from a 3rd Party Provider
Document Hash
Activity Factory adds a signature page and calculates the Cryptographic HASH of the file.
A HASH is a mathematical algorithm that calculates the file bits into a fixed string value (HASH). It is a one-way calculation and cannot be inverted.
So when someone tampers with a document it will result in a different HASH value.
3rd Party Digital Signatures
3rd Party Digital Signatures are recommended as they are validated by a 3rd Party Provider and is globally accepted.
Activity Factory Digital Signatures are provided by our partner Global Sign.
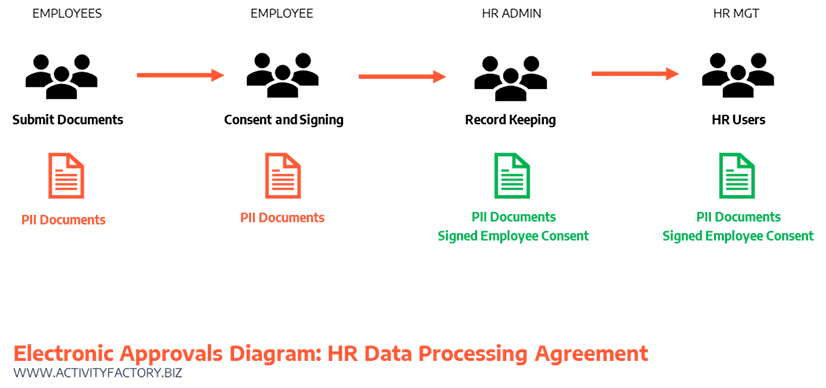
Minimizing the Cost of PII Compliance
Is this familiar?
- Gathering paper documents from employees (SSS Forms, EIS, BIR Forms, Resumes, Drug Tests, etc)
- Producing and printing consent forms
- Getting employees to sign the consent
- Storing all of these in folders
- Determining the completeness of the documents by the employee.
This is HR at its worst state, consuming all strategic time to paper pushing. Workflow automation solves this problem by gathering documents and consent electronically with a bonus of producing the compliance reports by using a document management system. The purpose of signatures is to validate and authorize a transaction, obviously done by physically signing the document. Electronically signing documents follow the same principle and are exposed to forgery just like traditional signatures; hence the use of Cryptographic approaches to digital signing.
Usernames and passwords are not enough
We strongly recommend the use of One Time Passwords (OTP) when moving into digitally signing documents.
OTP provides an added layer of security by using a user's mobile phone to ensure the identity of the user.
Digital Transformation and Compliance with Digital Signatures
For most companies, digital transformation has been a key part of their corporate strategy, and digital signatures are one of the areas that present a great opportunity in propelling this shift. Employees spend countless hours chasing ink signatures and approvals, and having to print, scan, fax, or e-mail documents afterward which can be lengthy and prone to process delays. The concern that arises is adopting digital signatures while ensuring compliance with the ever-changing business regulations.
Digital Signatures with Activity Factory
Activity Factory offers security features designed to protect business documents. However, the documents do not receive the same protection once it leaves the system. With the level of technology that we currently have, it also has become easy to forge and make unauthorized copies of documents. Activity Factory has partnered with GMO GlobalSign to ensure the integrity and security of the business documents. It can help support compliance by validating and auditing digital signature history, providing non-repudiation, signer authentication, and data integrity as its core benefits.
Activity Factory is a workflow automation tool that allows companies to build consistent and auditable compliance and operational workflows, ensuring that the right processes are followed at the right time while staying compliant.

Say goodbye to manual tasks – automate your workflow and elevate your team's perfomance.

